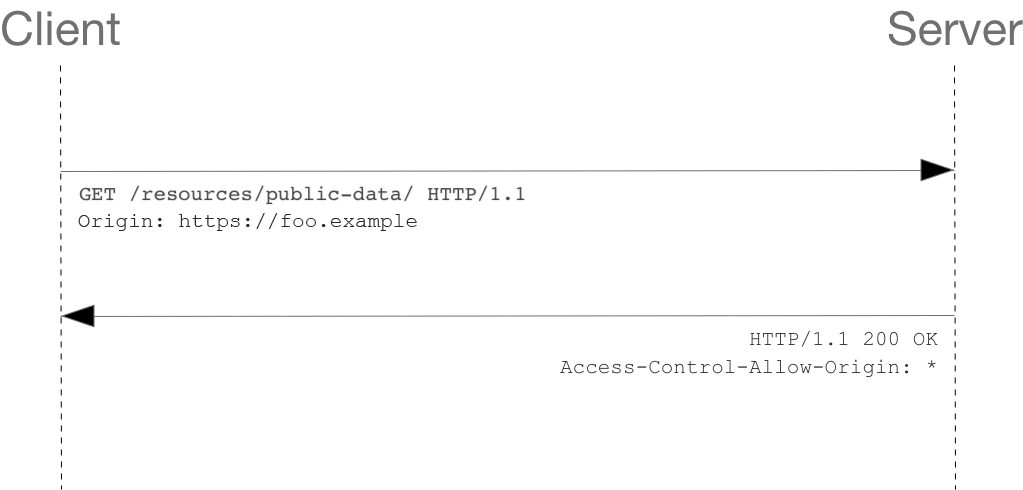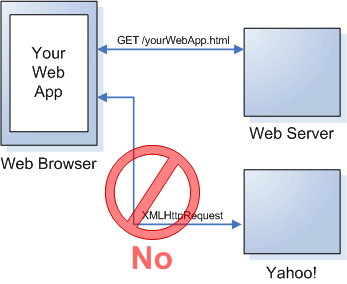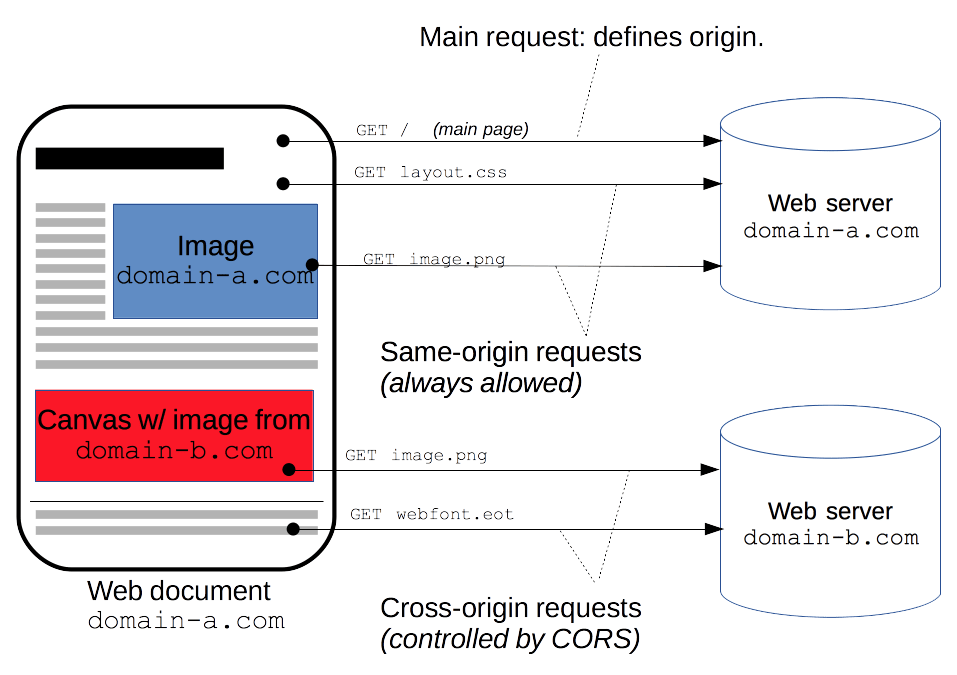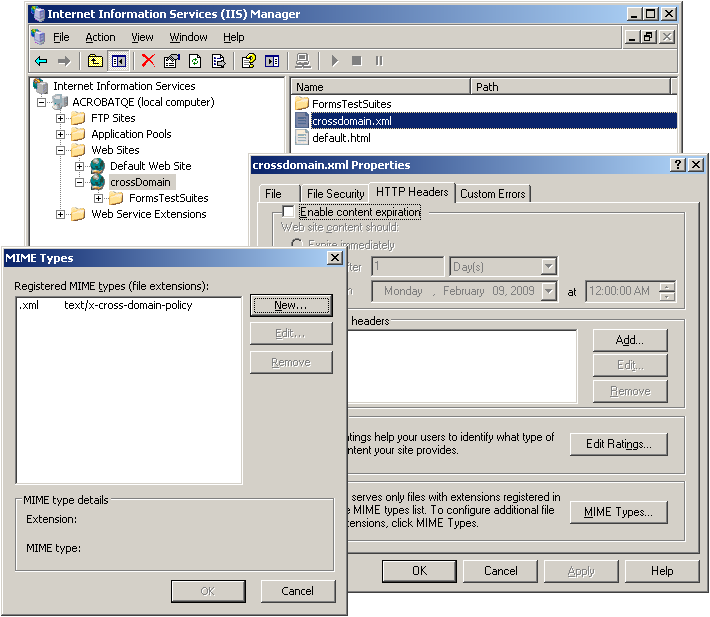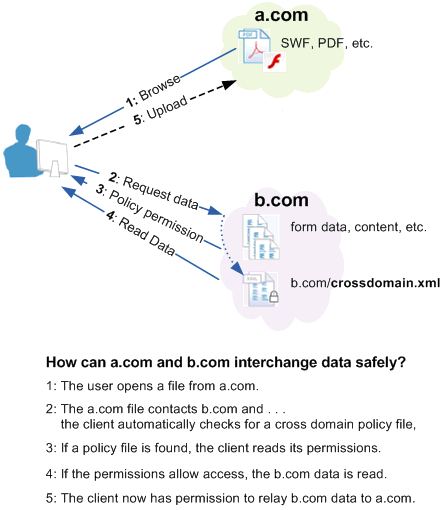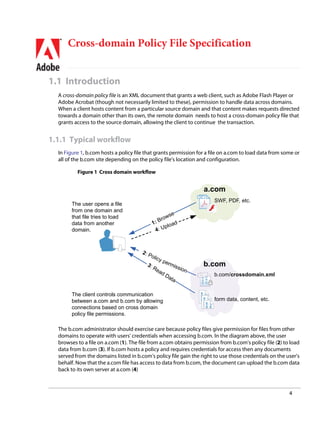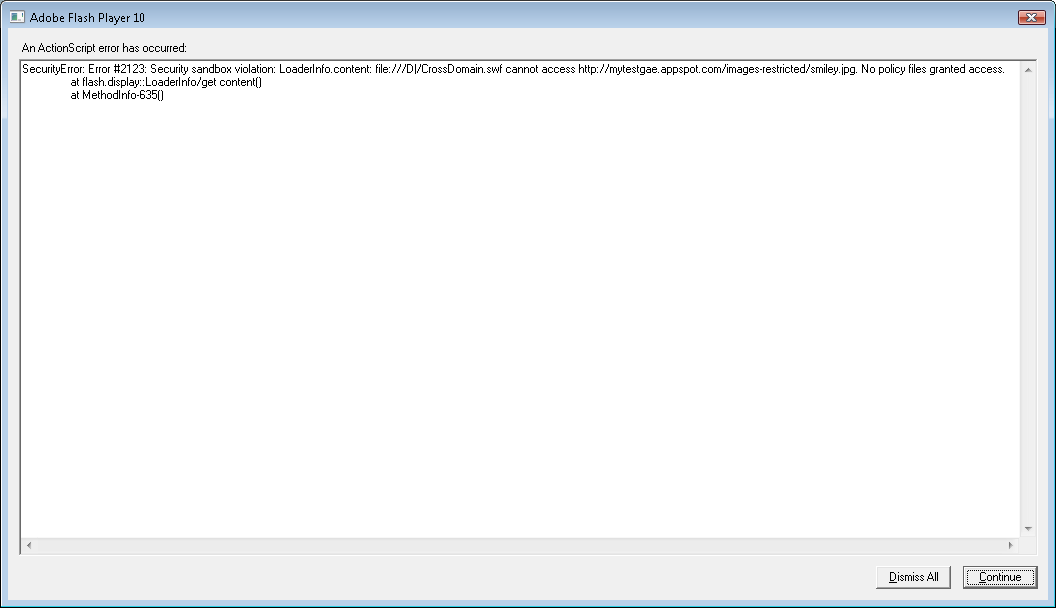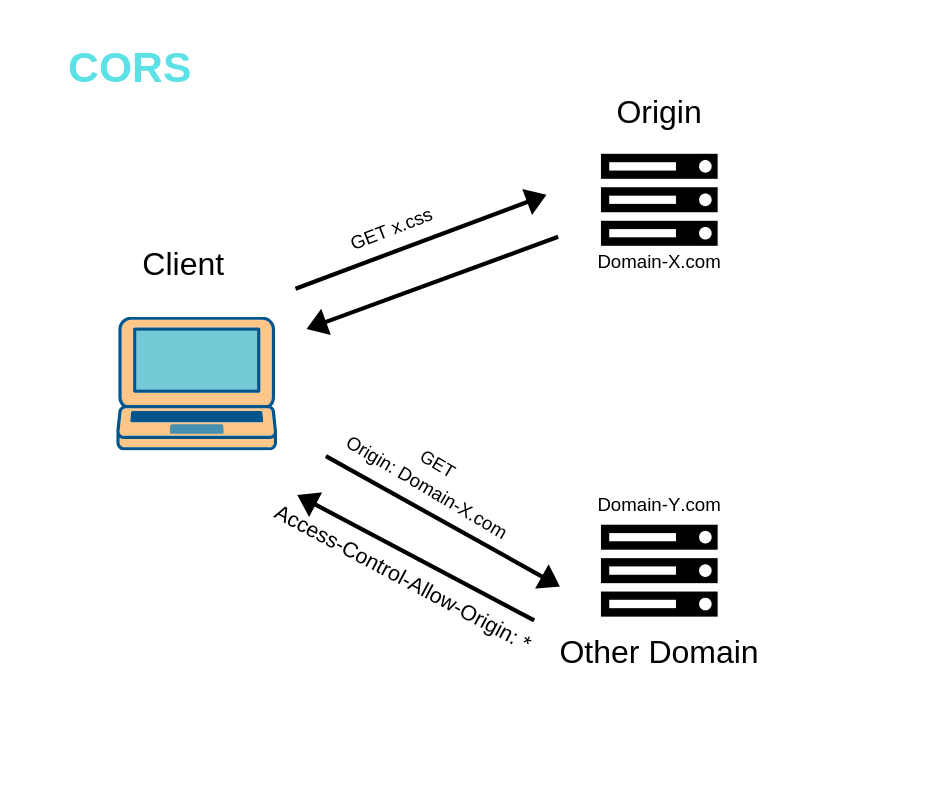
6 Must-Know Things About Cross-Origin Resource Sharing (CORS) | by GP Lee | JavaScript in Plain English
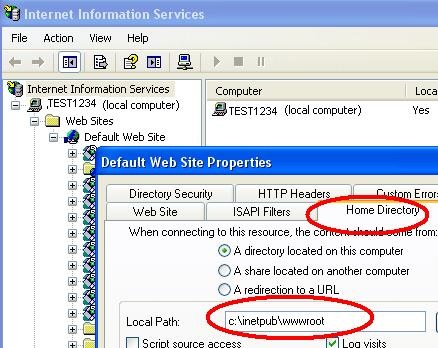
Using Silverlight 2.0 clientaccesspolicy.xml vs. crossdomain.xml for Web-Service cross-domain access - Cesar de la Torre

Insecure crossdomain.xml Policy file vulnerability – Learn Penetration Testing & Ethical Hacking | Julio Della Flora
![PDF] An empirical study on the security of cross-domain policies in rich internet applications | Semantic Scholar PDF] An empirical study on the security of cross-domain policies in rich internet applications | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/8b988165c663836cc5de52df21fa7c3b528e269d/5-Figure6-1.png)
PDF] An empirical study on the security of cross-domain policies in rich internet applications | Semantic Scholar

![PDF] Analyzing the Crossdomain Policies of Flash Applications | Semantic Scholar PDF] Analyzing the Crossdomain Policies of Flash Applications | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2d3f01f83330c1878411004fb5dc979ddd7440d2/4-Figure3-1.png)